Simflofy Architecture
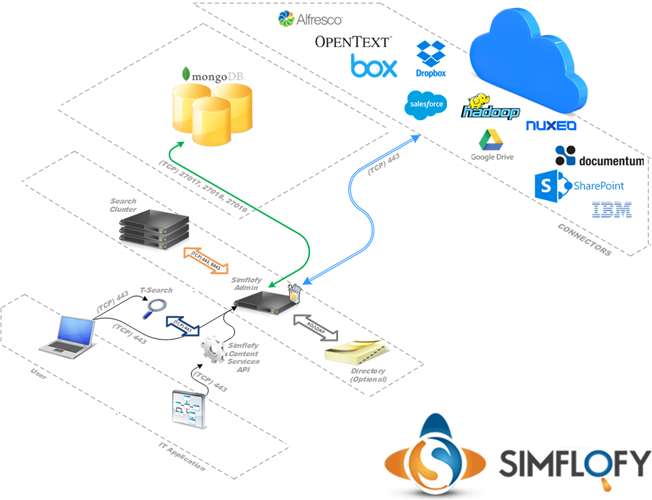
Simflofy Components
- Simflofy Admin
- T-Search
- MongoDB
Example Endpoint Integrations
- Filenet
- CMS
- File System
- FTP Server
- SSH Server
- Relational Database
- NoSQL Database
- Hadoop
Network and Firewall Requirements
Simflofy Admin
- Listen (TCP) Ports 80 and/or 443
- Communicates with MongoDB on (TCP) ports 27017, 27018, & 27019
- Communicates with T-Search on (TCP) port(s) 443 and/or 8443
- Optional: Communicates with Active Directory on ports: (TCP, UDP) 445, (TCP, UDP) 88, (UDP) 389, (TCP, UDP) 53
- Optional: Communicates with LDAP on (TCP) 389, (TCP) 636
Note: Communicates with CMIS and/or ECM platforms using vendor documented ports and procedures.
T-Search
Listen TCP Ports 443 and/or 8443
Communicates with Simflofy Admin on (TCP) ports 80/443
MongoDB
- Listen Ports 27017, 27018, & 27019
Certificates
Simflofy Admin & T-Search:
- Please refer to the following link Tomcat SSL for documentation of how to generate and enable SSL certificates.
Access & Permissions
Simflofy Admin & T-Search:
- Windows Local or Domain user with Read/Write permissions to Install and Tomcat Temp directory
- Linux Local or LDAP user with Read/Write permissions to Install and Tomcat Temp directory
Passwords and Encryption
Database Password
- In the simflofy-global.properties file there is an option to encrypt the database password:
simflofy.encrypt.db.passwords=false - Setting this to true will encrypt passwords using Simflofy's default encryption.
Connector Passwords
- All fields marked as passwords in the Simflofy UI are encrypted in the database and never returned to the User Interface.
Encryption Strength
By default, Simflofy will use whatever the default encryption strength is for Java. If you wish to use the more secure AES 256, you will need to do 2 things:
- In the simflofy-global.properties file, set this setting: simflofy.aes256.encryption=true
- Install the JCEK policy file. JCE Unlimited Strength Jurisdiction Policy Files 7 Download
- For 256 you need the unlimited Strength Jurisdiction Policy file below. In some countries you will not be able to use this file. AES-256 Encryption with Java and JCEKS
Related Articles: